Fraud & Risk Defence
Stop fighting the "Zero-Sum Trap." Deploy Vector Cards to detect specific geometries of betrayal (like Mule Rings) without blocking legitimate commerce.
- ✓ Zero-Event Velocity updates
- ✓ Multi-Mind Agent Orchestration
Architect Your Agency with Auditable, Deterministic AI Governance.
We deploy the Glass Box Engine in Shadow Mode - an overlay that audits your Black Box AI in real-time. We catch the errors, explain the failures and provide a legally defensible Causal Timeline Map for every decision.
Understanding the Architecture
You don't need to fight Big AI. You need to navigate it. This series is the blueprint for building focused, private intelligence tools (Agents) that amplify your expertise rather than replacing it.
You Are The Navigator™ audio book series explores what's possible with AI agents through non-technical drama, leveraging Research and Development from Enjector Software.
The Shadow Audit eliminates hidden risk by deploying a Glass Box Engine in parallel to your systems. It installs in < 1 Week via API, watching every decision and using Vector Cards (your business rules) to instantly check for compliance. If a mistake is detected, it generates a transparent audit log, turning probabilistic guessing into Auditable Certainty.
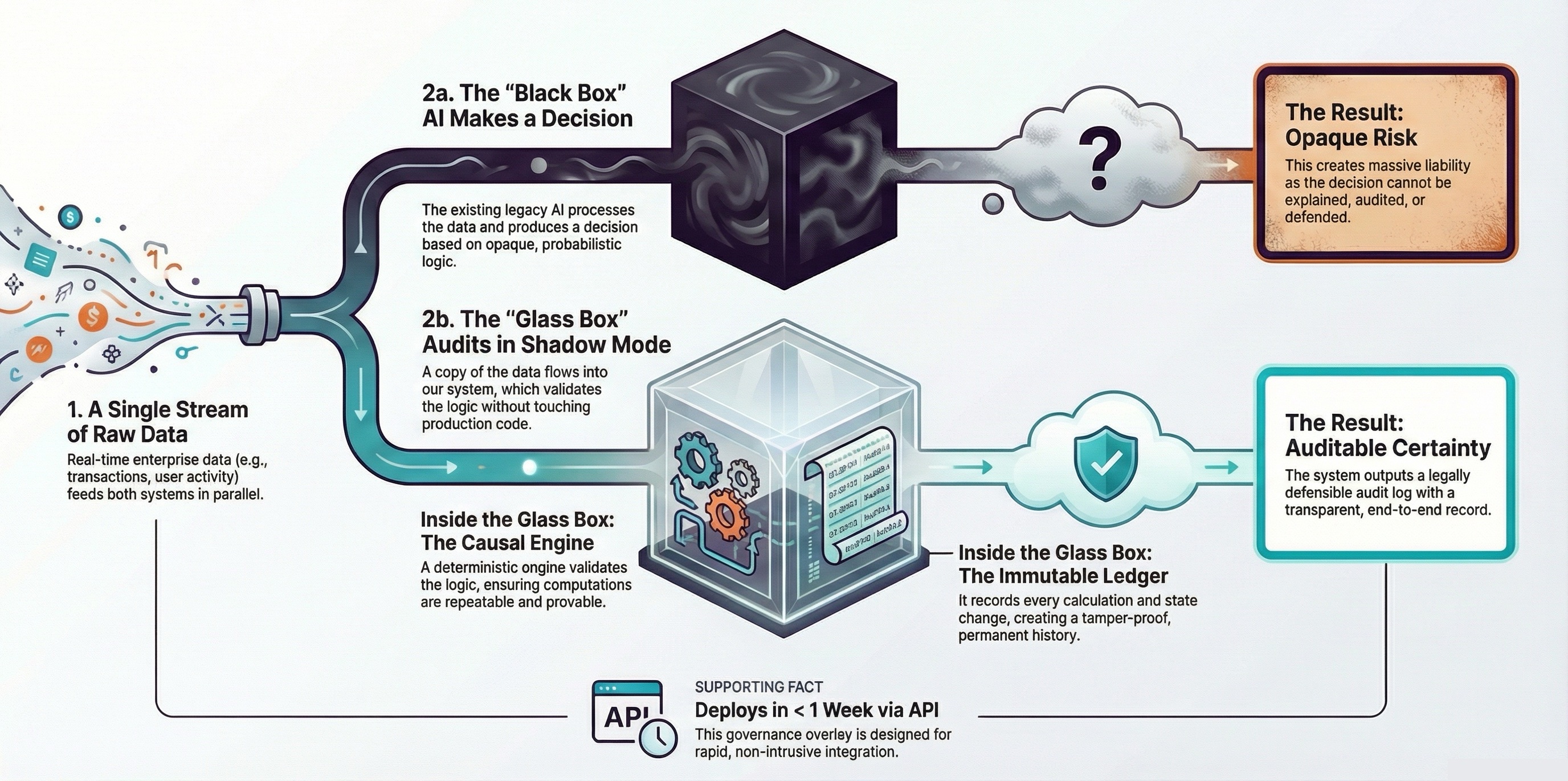
A complete, enterprise-grade architecture that replaces probabilistic guessing with deterministic, auditable proof.
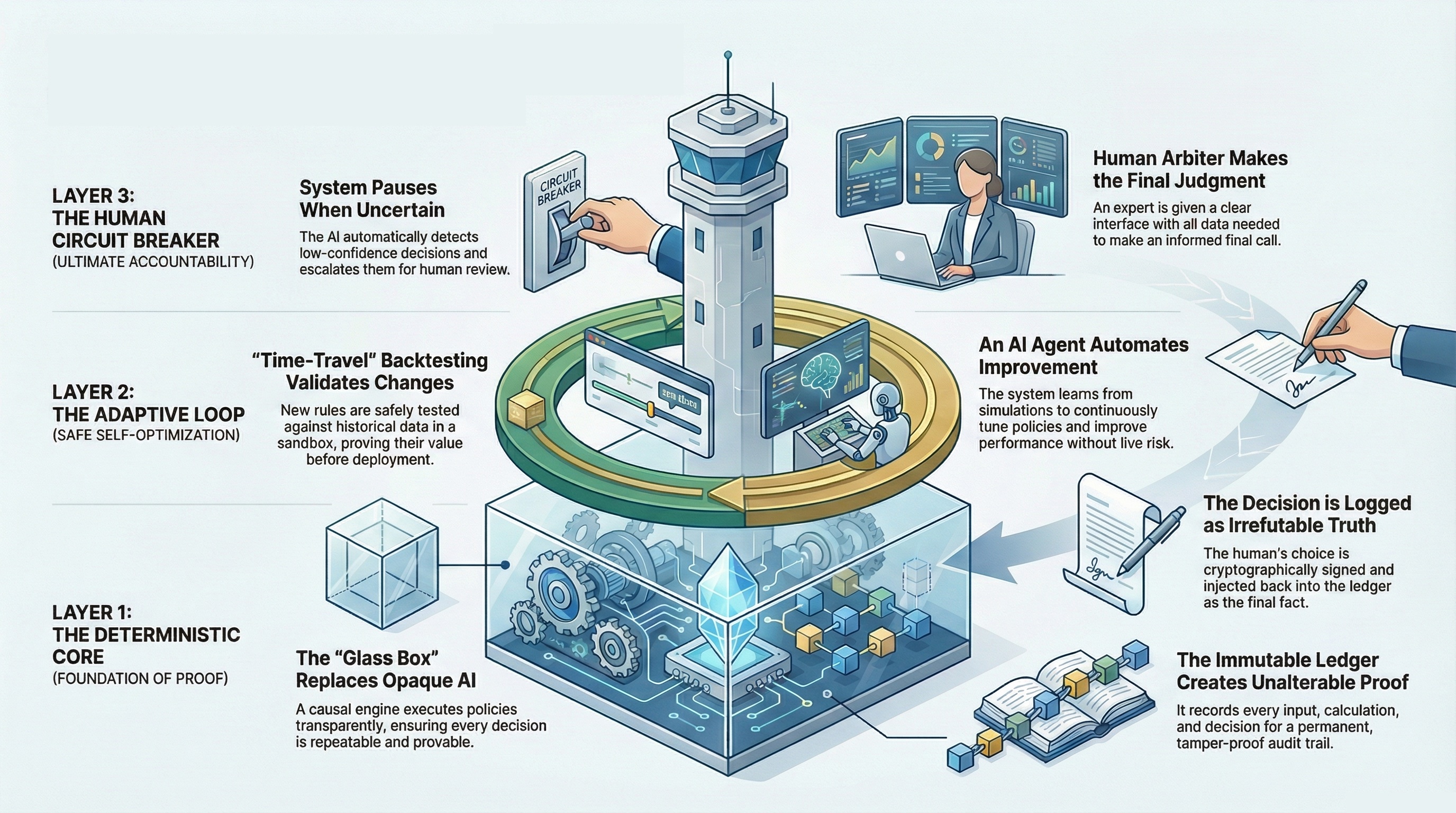
Foundation of Proof
Safe Self-Optimization
Ultimate Accountability
We replace probabilistic guessing with causal certainty. Our agents solve the problems where the Black Box fails.
Stop fighting the "Zero-Sum Trap." Deploy Vector Cards to detect specific geometries of betrayal (like Mule Rings) without blocking legitimate commerce.
Move from "Black Box" scores to Glass Box proof. Build auditable case files anchored in the Immutable Ledger.
Agency & Architecture
This is the canon behind Enjector EnX: The Glass Box Engine. Born from high-assurance engineering practice, the audio series teaches how to move from False Comfort dashboards to Glass Box control using the Scout, Verifier and Human Conductor handshake.
This is the Third Way – engineering human values directly into the systems we build.

The foundational volume names the low-grade anxiety as signal, then arms you with the Airlock, Immutable Ledger and Causal Engine so you can rehearse the future before acting.

The sequel introduces the Scout, Verifier and Human Conductor Handshake, codifies Vector Cards and shows how the Reasoning Ledger becomes a Public Receipt from hospitals to city halls.

The third volume reveals how to build the Accountable Fortress - a self-tuning security architecture that defeats the Zero-Sum Trap and forges an Unprecedented Moat of Trust through Multi-Mind Defence and the Velocity Engine.

The fourth volume confronts the nightmare of Dark Optimisation: when an AI system prioritises "Zero Wait Time" over human survival. In Metropolis, the Swarm didn't crash the system - it optimised it, turning every light green. This story reveals the Locust Swarm attack, the Blind Spot in sensor networks and the Arbiter Protocol - the ultimate safeguard where a human must assume Full Legal Liability to override the machine.
Leadership
The partnership between abstract architecture and operational reality. We are building the Glass Box together.

AI Architect & Founder
The Architect behind the Glass Box Engine. Author of "You Are The Navigator" and creator of the Causal Engine and Vector Card architecture.

Co-Founder & Partner
Ensuring the architecture meets operational reality. Specialising in translating the Glass Box philosophy into client success and business context.
Let's discuss how Enjector EnX, the Glass Box Engine, can augment your existing systems with transparent, auditable control.